In the past, if you incorrectly typed in the name of a website you might have landed on a parked domain pretending to offer content. The website owner got some ad revenue and you got a small detour. No real harm was done to either party. These days I’m landing much more frequently on the scam websites that attempt to hijack your browser, and trick you into calling a number purporting to be the Microsoft Support Center (it isn’t) and letting some crook aka support agent get access and control of your computer. Do not let that happen or you could be in big trouble. Sometimes, the page will look like the one below. It will attempt to get you to call a number with a female voice advising you to speak to a so-called “agent”. Never call these freaks. These messages are bogus and the page is not detecting any problem on your computer. The same error message is displayed to anyone unlucky enough to land there. If you fall for this scam, you are opening up you and your computer to a big can of worms.
What could happen?
If you provide them access to your computer so they can “fix it” they can steal your personal information or hold your computer ransom by asking for money to unlock it. Sometimes they are bluffing about locking your computer and you can escape. I’ll tell you how to escape in a bit.) There are two variations on this scam. The fake ransom attempt holds your browser captive by locking your browser. You won’t be able to go back out or go forward to another site. Other variations of the scam include scammers calling you from a local or US Skype phone number to get you to use their support service. They can be friendly but when you don’t pay they will get angry. If they have only trapped your browser session you can tell them to take a hike. You are actually lucky. You’ve only been tricked into thinking your computer is being held ransom.
The most serious of these scenarios is an actual Ransomware play where the bad guys get on to your computer because either you’ve given them access or you clicked on an email link which took you to a malware loaded website that contained a form of Cryptoware which immediately encrypts (locks down) your computer’s data. In this case, you have limited choices because you are left with a crippled computer . All of your photos, apps, and just about everything needed to make your computer function is encoded/encrypted and you can no longer be used unless you wipe it clean and reinstall a new version of your operating system (OS). If everything is backed up and you don’t mind restoring and reinstalling Windows or a Mac OS and all your apps then you call tell them to shove it where the sun don’t shine.
If you haven’t backed up your data you are out of luck. You might need to take a 30 minute walk to chill out before you blow your top. If you don’t pay the ransom you will most likely lose all of your data. (Sermon) If you are not backing your computer up to an external hard drive and to a cloud storage service daily you are playing “Russian Roulette” and will probably lose your data at some point in time. Please play it safe. Backing up your data will also help you or someone working with you to recover you PC if should you have a computer problem down the road.
Here’s a link to get you started. Ransom is usually requested by some anonymous method. For individuals, Western Union is the usual payment service request. Businesses are usually asked for payment in “Bitcoin” since it is virtually untraceable.
If you have been trapped into a locked browser session, when you try to escape you will often find your browser seems to be locked. Don’t panic. If you haven’t been infected by a real Ransomware program you can easily get out of this trap. Note: Most Ransomeware attacks are initiated through sophisticated socially engineered emails which often has legitimate personal information and looks so authentic the immediate instinct is to click on a link. As my friend Stu Sjouwerman, CEO of
Knowbe4.com probably says in his sleep. “Think Before You Click.”
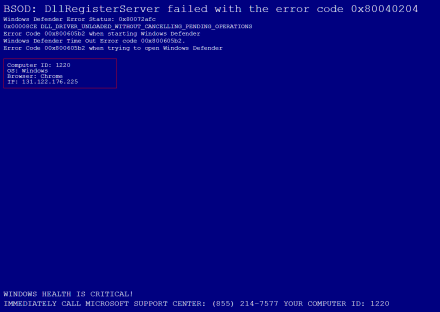
How To Escape From A Fake Ransom Page
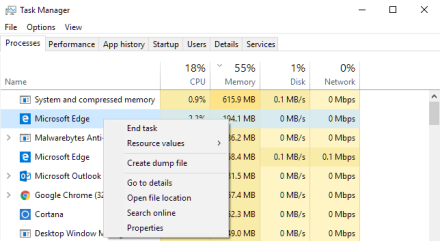
Using Windows, If you hold down the CTRL_ALT_DEL keys at the same time you will launch Windows Task Manager. Then find your browser in the list. Highlight your browser. Right click and End task. You should now be free.
If you are using a Mac you will probably need to end the Safari browser task. You can do this by pressing the Command ⌘ + Option + Esc. Select Safari. The press Force Quit.
Similarly, if you’re using an Android Smartphone you’ve may have encountered a similar situation which says your Android phone is infected with a virus and the browser session is locked. You can try restarting your phone. If that doesn’t work end the browser session by killing the task. You can either download a Task Manager from the Google Play Store or you can just go into Android settings. (The menus will vary by Android version. This screen shots below are from version 5.1.1. Go to Applications and STOP the particular browser you’re using. Click on the Application. In this case your browser. Then click on FORCE STOP. This will kill the browser task and free you.
Ransomware “The Real Deal”
Ransomware is becoming a big money-maker for Cyberthieves. The average ransom demand is between $200 and 10,000 according to the FBI aimed at both individuals and businesses. These scams use sophisticated socially engineered fake (phishing) emails. These often contain personal information about you that they have obtained from the “Dark Web” (I’ll explain the Dark Web in another blog post). When presented with an email that seems to know a lot about you an unsuspecting employee is tempted to click on an attachment or a link to a web site which installs ransomware malware. It then releases a program designed to encrypt that PC’s data.
Cyberthieves trade or sell millions of personal identity theft info among themselves that they’ve obtained through prior hacks. According to the Privacy Rights Clearing House, 898,458,345 records have been breached from 2005-present! That’s a huge amount of personal data to work with. Cybertheives target businesses, non profits, police and government sites, and hospitals are now getting hit frequently. The cyber thieves encode (encrypt) the data and ask for payment in bitcoin to unencrypt the data. It is virtually impossible to unencrypt the data without the encryption key the crooks aren’t going to give that to you without payment. While the NSA may be able to unencrypt them using a super computer it would probably cost a fortune and very few entities have access to that kind of computing crunching power to break strong encryption. Many companies end up paying the ransom fee when faced with the cost of trying to reconstruct the data in addition to the outage time if they haven’t had up to the minute transactional backups.
Resources:
FBI official page on Ransomware.
Ransomware on the Rise – FBI
Security Awareness Training and News – CyberheistNews
The National Institute of Standards and Technology (NIST)
Google News Search Results for Ransomware
Tools
BitDefender Crypto-Ransomware Vaccine





